There’s a problem with mobile biometrics. More specifically, there’s a disconnect between how they should be used, and how they are being used. App developers are treating a fingerprint as though it though it will 100% surely assert that the user is who they say they are when in reality it can’t, it can only assert that they had access to the phone at one point or another. Looking at Android for specifics, let’s look at why the problem is there, and how it can be fixed.
A brief history
In 2007 the Toshiba G500 was released. Running a version of Windows for mobile that vastly predates the tiling phone OS we associate with the name today, the device is alleged to be the first mobile phone with a fingerprint scanner. Fingerprint scanners of this era were all optical and if they’re anything like the ones I’ve used, a bit hit and miss. At the time it was somewhat of a novelty and almost exclusively used to unlock the phone. 6 years pass, and along came the iPhone 5s in 2013 with the now more widely used capacitative style sensor. Again, using it (at first) as a convenient and quick way to unlock your phone. The rest, as they say, is history. As of 2018, 70% of all smartphones shipped will be equipped with a fingerprint scanner. [1]
So what’s the problem?
The issue is that because adding a fingerprint is protected only by the lock screen password, and fingerprints are not revoked during a lock screen password change, a valid fingerprint is less a certain assertion it’s the device’s owner and more proof that whoever is holding the phone once knew the device password. Even if it’s since been changed. As such, applications using fingerprints to assert the user’s identity are also giving access to anyone who has ever know their lock screen password. The difference between ‘Authorised to access the device’ and ‘Biometrically proven to be the owner’ is a subtle, but important differentiation.
An obvious use case here is that many couples, friends, and siblings have access to each others phones, usually because they borrow it from time to time. For me this is true, I know the password to a few of my friends phones. Now whilst these people may not have an issue with me unlocking their phone read a message to them whilst they’re driving, or so that I can show them the latest viral video, they most likely don’t want me having access to their banking applications or paypal etc. But once I know their password, pattern, or pin, I almost always have access to all of this.
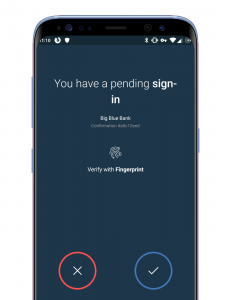
But if you’re sharing passwords, you can’t expect privacy!
So the obvious retort to the above example is that if someone has knowingly given me the password to unlock their phone, shouldn’t they expect that I’d be able to access everything? This isn’t, however, true if you use passwords for everything. For example if you have a password on your banking application it can be set to a different password to the one on your phone or your paypal account etc, and everyone knows that password reuse is a bad bad security practice.
The point is passwords allow you to enforce a finer-grained access control across your accounts than fingerprints allow for, and assuming that the fingerprint proves the identity of the user is a bad idea. Fingerprints are better usernames than they are passwords.
Adding fingerprints is not fingerprint protected
Let’s look at a quick scenario. Bob is setting up his new phone, and he installs paypal. Paypal asks him to sign in with a username and password and Bob, being security aware, has a unique 20 character password only used for Paypal. Now, once installed it prompts him and asks ‘Use fingerprint to unlock app in future’ and bob ticks ‘yes’ to save time. So far everything is fine, but now, when Alice asks to use Bob’s phone, he gives her the lock screen pattern. By knowing the pattern to his lockscreen, Alice can now add a new fingerprint and subsequently can use her fingerprint to login to every app allowing fingerprint logins, an umbrella under which most banking apps fall under.
Fingerprints are being used my many apps to assert the person holding the phone’s identity, when currently it can only verify the person knew how to unlock the device.
Fingerprints persist password changes
Lastly, when you update your device password in Android the registered fingerprints stay on the device. I personally have 2 fingers enrolled on my phone, such that I can unlock in with either hand. But considering I unlock my device with my left hand about once every 3 months, how do I know someone who knew my old phone password didn’t delete my left fingerprint and enroll their own? I doubt many people check the fingerprint settings often enough to know if a new finger or two had cropped up. This therefore means that changing the password on your phone does not guarantee retracting access to anyone who previously had it.
Android tells apps when the fingerprint data updates, doesn’t it?
Whilst the Android fingerprint API can tell the app that fingerprint information has been updated, and that the app should force password authentication again, I’ve seen several apps that don’t act on this. In my tests, my Nationwide banking app did prompt for password re-auth, but Monzo, Nextcloud and a few more did not.
Furthermore, it does not alert the user that it’s asking for a password because the fingerprint information has changed, so many users would simply enter their password and continue to use fingerprint authentication.
It’s not the end of the world. But it’s not great either.
I want to make it clear that I don’t think this is the end of the world. In many cases, banking applications that allow unlocking with a fingerprint won’t allow you to add a new payee without further step up authentication, so you can’t see someone’s screen pattern then steal all their money. I do think it is somewhat of a process flaw though, you should be able to grant a person access to the unsecured apps on your phone without relinquishing access to the secure and often private information in other applications.
How do we fix it?
Option 1 – Two types of fingerprint
The first option is to have two types of fingerprint, one which can unlock your account, and one which can assert your identity.
In this scenario you would have to have a ‘master fingerprint’ that you scan in order to allow a new fingerprint to assert your identity, but this does come with a whole host of other issues. When dealing with fingerprints you can’t rule out that there’s going to be a scenario where a person no longer has access to their master finger. Accidents happen.
This option avoids having another password for the user to remember (after all, isn’t that part of the point of fingerprints?), but it’s not the cleanest.
Option 2 – A master password for fingerprint adding
Option 2 is a simpler approach to the above: Simply require a master password to be set when you first configure a fingerprint on the OS, and then require this password instead of the lock screen password in the future. This would be my personal approach as it’s simple and easy, but adds an extra layer of security.
Option 3 – Don’t use fingerprint authentication
Of course, there is always the option not to use these systems. Leave your Nationwide, Paypal or other banking app password protected. Lose the ease of use of a fingerprint for the fine grained security of a password. A lot of the time security is little more than complex risk mitigation and, if you have something you really need to protect, a password is a lot more secure than a fingerprint
Wrapping up…
Fingerprints are great for certain things. A second factor to accompany a password, being the username to a traditional password, a convenient way to unlock a device. However, due to the way that Android uses the same password used to unlock the device to add new fingerprints (fingers on what it falsely presumes to be the same person), they are not suited to verify with 100% certainty that it’s the phone owner holding the device. They’re really acting more as a token that proves the person scanning their finger knew the device password at one point or another. A master password on the fingerprint setting would be the easiest fix, and something I’d like to see in the future.
On most phones, a way of dealing with this would be to use the Google account / iCloud password. This way you don’t have yet another password to remember, but you still gain the additional security.
On Android at least,, every fingerprint authenticated app I have used, if a fingerprint is added or removed, say “your fingerprint authentication has changed, please relogin using your password”
That’s a good point, and perhaps something I should’ve included in the post, however it not that explicit. It’s true that most apps will make you login with a password again, and if it did explicitly saying ‘A new finger was added’ that would be great, but currently many people would see the prompt, put the password in without thinking and therefor allow someone who’d added a finger to come back and log in later.
I don’t know how many apps use this but LastPass on android detects when a fingerprint has been added or removed and will completely sign you out.
Your X230 was from 2013 , 6 years later being a 3rd gen machine,
I have never found it to be hit and miss in the fingerprint scanner department.
Just an opinion from someone that has worked with and on Lenovo products and a bunch of others for some considerable time now.
Interesting. Do you run windows or linux on it? I’m running ubuntu 16 on it using fprintd for the fingerprint software. I can enroll fingers but it only seems to read them correctly about 30% of the time.
I’m pretty sure that at least in Oreo fingerprint management is password protected at least, so if I unlock and lend my phone they can’t mess with the fingerprints… and there’s also screen pinning for lending.
Wouldn’t the easiest solution to the downside of option 1, be to have a backup password in case you… lose access… to your master finger? If you lose your master finger, you can type in your password iH8ipH0N3s, or your Google/Apple password to regain access to the fingerprint page?
Moral of the story, master/admin fingerprint to unlock apps and the device and add fingers, regular fingerprint to unlock the device. Lose the finger, use a password to change it.
Plus, in this master fingerprint scenario, there would HAVE to be a way to change the master fingerprint without the master finger. Like any password, it can be changed when “forgotten”.
I have not had to change app passwords when adding new prints, but I only use 2 apps that use prints. I do wish one of them (encrypted sms) would use a password, or combination. it’s good they max out at 4, although I kind of wanted to do my whole hand since I hold my phone in different ways for different tasks, and to alleviate fatigue, but ofc that lowers security potentially further. I suppose the same issues exist with iris scanners. I generally have no reason to worry about my phone being tampered with, but do use a complex and visually confusing pattern lock, should probably use a password too, and I require the pattern lock to decrypt the phone on startup. long as no one gets access to fingerprint settings AND the pattern or password (PIN seems the least secure), all should be well, but these are good points and the protocol could easily be more secure. I like the idea of fingerprints being the username rather than the password, that would truly increase security.
Hello. impressive job. I did not anticipate this.